Business Email Compromise (BEC) attacks are cybercrime attacks in which attackers impersonate senior executives, leaders, and managers associated with a business and trick employees into transferring money or sensitive information to fraudulent accounts.
These attacks have emerged as a significant cybersecurity threat that has resulted in financial losses for organisations worldwide.
According to a recent report by Trend Micro, “‘Pretexting’ The Next Cybersecurity Epidemic?”, Business Email Compromise (BEC) attacks reported to the FBI in 2022 cost organisations over $2.7 billion.
That’s more than a quarter of total cybercrime losses!
This staggering figure highlights the need for business leaders and management professionals to understand the nature of BEC attacks and take proactive measures to protect their organisations.
Unlike ransomware attacks, which usually garner media attention due to their disruptive nature, BEC attacks are more insidious and can go undetected for long periods.
The report reveals these attacks are, on average, more than eight times as profitable for attackers compared to ransomware, with an average of £99,231.34 per attack versus £11,375.76 for ransomware.
As cybercriminals adapt and employ more advanced technologies like AI-powered deepfakes to make their schemes more convincing, senior leadership must act urgently, and get informed about the evolving landscape of cybersecurity threats.
By understanding the scope of the problem and implementing a comprehensive approach that addresses: People, Processes, and Technology.
Business leaders can strengthen their cybersecurity initiatives and safeguard their companies from the financial and reputational damage caused by BEC attacks.
How Do BEC Attacks Work?

We’ve laid the groundwork for the costly nature of these attacks.
Let’s see what the report says about how these scams work.
The Trend Micro report gives us a detailed look at the tactics cybercriminals use to trick their targets, and it is eye-opening.
At the heart of BEC attacks is pretexting, a fancy term for social engineering in which attackers attempt to manipulate, influence, or deceive people into performing actions or divulging confidential information.
In BEC attacks, criminals pose as senior executives, management, or someone trusted in the company.
They use this fake identity to pressure and force the victim (often an unsuspecting employee) into transferring money to a fraudulent account.
The report reveals how pretexting incidents have doubled in the past year, making it more common than phishing.
Scammers Do Their Homework
But how do these attackers make their scams so convincing? They do their homework, that’s how.
They gather publicly available information about their targets from all over the web including corporate websites and social media.
These are some of their starting points.
They use this information and more to craft messages that seem scarily convincing and create a false sense of urgency.
The result: The targeted person feels pressured to act quickly, often without double-checking if the request is actually genuine.
The Sophisticated Use of AI
The report also highlights how cybercriminals are starting to use AI and deepfake technology to make their BEC attacks even more believable.
Attackers can add an extra layer of “trust” to their scams by using AI to mimic someone’s voice or video.
In one case, scammers tricked a British CEO into wiring an attacker $243,000 by using deepfake audio to impersonate his German boss. Pretty wild stuff, right?
As BEC attacks evolve and technology advances, it becomes increasingly urgent that organisations understand these techniques and implement measures to spot and stop them.
Why Are Companies So Vulnerable?

The Trend Micro report highlights two key factors contributing to the success of BEC attacks:
Hierarchical corporate structures.
Lack of proper business processes.
In some organisations, especially those with strong hierarchical structures, employees tend not to question or challenge requests from senior executives.
The report notes in founder-managed companies, the word of senior executives is often considered gospel. No wonder employees find it difficult to push back on suspicious requests.
Cybercriminals exploit this power dynamic by impersonating high-level executives and pressuring lower-level employees to comply with their demands.
The report also highlights how gaps in business processes can leave companies vulnerable to BEC attacks. In some cases, large financial transfers may not require multiple approvals or even thorough verification.
Fraudulent requests slip through the cracks in such situations. Without proper checks and balances, one employee can unwittingly transfer large sums of money to these attackers.
Cybercriminals Are Skilled Professionals
Moreover, cybercriminals’ technical skills drive the success of these attacks.
Attackers are adept at spoofing email domains or even hijacking executive email accounts through phishing attacks, allowing them to send convincing emails that appear to originate from legitimate sources.
Combine this with the social engineering tactics used to create a sense of urgency, and it’s no wonder many employees fall victim to these scams.
A combination of human factors and process gaps clearly contributes to companies’ vulnerability to BEC attacks. Recognising these weaknesses is the first step in developing effective risk mitigation strategies.
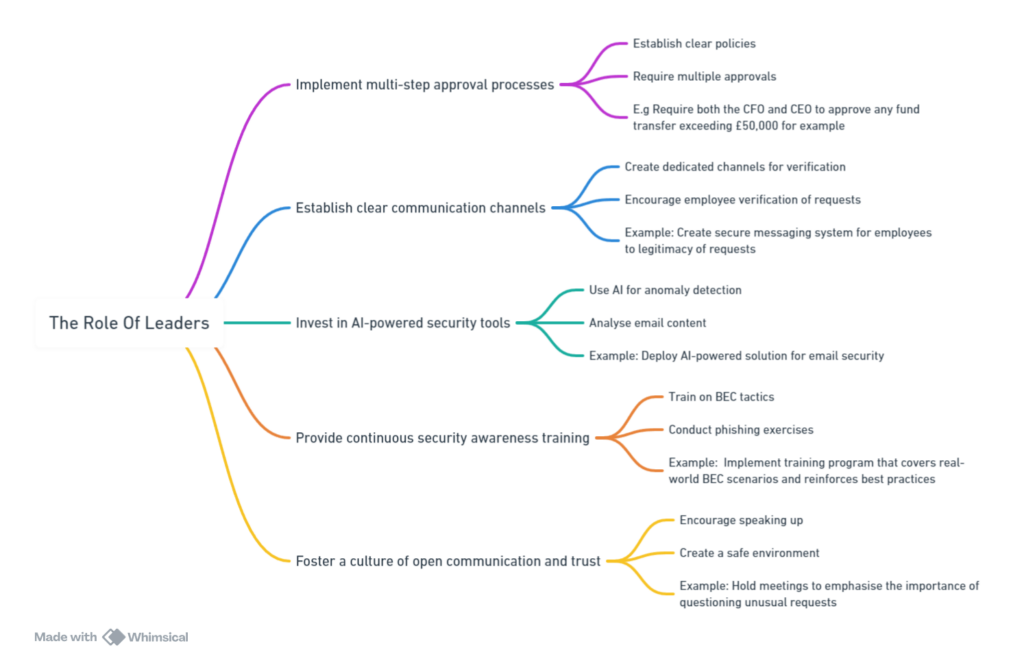
What Should Leaders Be Doing To Protect Their Organisations?
The Trend Micro report offers insights and recommendations to help fortify your defences against these costly scams.
The Growing Threat of BEC Attacks
In this blog post, we’ve learnt of the growing threat of Business Email Compromise (BEC) attacks and the financial impact they can have on organisations.
The Trend Micro report “‘Pretexting’ The Next Cybersecurity Epidemic?” has provided valuable insights into cybercriminals’ tactics, the factors that make companies vulnerable, and the steps leaders can take to protect their companies.
We’ve learned that BEC attacks often rely on pretexting and social engineering techniques.
Attackers impersonate people to trick employees into transferring money to fraudulent accounts.
The increasing use of AI and deepfake technology has made these scams even more convincing and difficult to detect.
Furthermore, we’ve seen how hierarchical corporate structures and a lack of proper business processes can leave companies vulnerable to these cybersecurity attacks.
Cybercriminals exploit power dynamics and gaps in financial approval processes to carry out their scams successfully.
The fight against BEC attacks and other cybersecurity threats requires a collaborative effort from leaders, employees, and technology providers.
By staying informed, implementing best practices, and fostering a security-conscious culture, you and your organisation can help build resilience against these sophisticated scams and protect valuable assets in an increasingly digital world.